cfg parser
5/10/2018
I wanted to roll my own cfg/ini-like parser in C, it started off somewhat elegant to my low standards, however it quickly became a mess. It isn't great, but it "works".
It handles simple cfg/ini like files with 'key=value' pairs.
It's really hacky, I wouldn't really trust it for anything.
Comments are ignored, they're denoted by the '#' character.
Spaces are currently treated literally. test=123 and test = 123 are DIFFERENT, the key has a space appended and the value a space prepended in the second example.
Duplicate keys are not handled currently, the cfggetvalue function will only give you the first value.
See settings.cfg for an example cfg file.
To compile type make. Run the example program by issuing ./example.
All functions return 0 on failure, this goes for getting a value, always check 0 isn't returned. If it is, that means the key was not found.
Writing back to the cfg file is NOT implemented.
main.c has a usage example, however the usage structure is like this:
// allocate memory for the cfg structure
struct cfgfile *cfg = malloc(sizeof(struct cfgfile));
// setup cfg structure passing it the cfg structure we just made and a file name
cfgsetup(cfg, "filename.cfg");
// create a buffer for our value
char buffer[256];
// collect our value, the function returns 0 on a failure (when it cannot find the key)
int val;
val = cfggetvalue(cfg, "key", buffer, sizeof(buffer));
if (val != 0)
puts(buffer); // print our value
else
puts("cannot find the key!");
// free all of our memory (including cfg itself)
cfgfree(cfg);
The source is available in my git repository.


Binary clock
19/9/2018
To force me to learn recognising binary numbers easier I've created a small program that takes the current time and converts it to binary. I apply this binary string to the X displays root window title, dwm takes this string and puts it into the status bar, it replaces the decimal clock that was there before. Now if I want to know the time I have to convert it into decimal or spend the effort typing 'date' into a terminal.
The source is available in my git repository.


What am I doing?
18/8/2018
I don't know what I'm doing with my life. It's going no where and I'm up against a brick wall I just can't seem to get myself over, no matter how much I try.
At what point is it fair to give up?


x86 Assembly
16/7/2018
A little while ago I temporarily became interested in 8085 assembly and wrote a few little exercises and quickly lost interest. However, the basics were retained and I was highly interested in some day coming back to it.
Over the last few days I have been looking at x86 assembly (Intel syntax, NASM assembler) and have followed various tutorials and videos furthering my existing, yet basic knowledge. At this point I felt I was comfortable enough to attempt a small and simple exercise, I chose to generate Fibonacci numbers.
First, I wrote the program in C to understand the required logic flow.
#include <stdio.h>
int main(void)
{
int i, tmp;
int first = 0;
int second = 1;
printf("%d\n%d\n", first, second);
for (i = 0; i < 10; i++)
{
tmp = second;
second += first;
first = tmp;
printf("%d\n", second);
}
return 0;
}
Using the C version, I translated the program into x86 assembly: fibonacci.asm
%include 'functions.asm' SECTION .data MAX db 8 ; 10 - 2 (we print those outside the loop) SECTION .text global _start _start: ; eax -> first ; ebx -> second ; ecx -> counter ; edx -> tmp ; MAX -> maximum iterations mov eax, 0 mov ebx, 1 mov ecx, 0 mov edx, 0 ; print the first iteration of values (0, 1) call printintlf push eax ; store eax on the stack mov eax, ebx ; printintlf requires the int in eax call printintlf pop eax ; restore eax loop: inc ecx mov edx, ebx ; store second as tmp data add ebx, eax ; add first to second mov eax, edx ; set first as what second was (tmp variable) push eax ; store eax on the stack mov eax, ebx ; printintlf requires the int in eax call printintlf pop eax ; restore eax cmp ecx, [MAX] ; check if our counter has reached MAX, if it hasn't loop jne loop call exit'functions.asm' is a file containing some standard functions for string/int printing, exiting etc. I wrote the functions following the tutorials at asmtutor.com. You can find the file here if you care to see it.
I hope to spend considerably longer learning and writing programs this time.


Backup procedure
14/6/2018
A year or two ago I my bulk data storage drive died - it was 2TB and held information spanning back to around 2013 when I first got this computer. Of course, none of the data was backed up. I thought this would hurt, but it didn't. I've not thought twice about the data I had lost. I guess none of it was important.
Today, things are a little different. I keep semi up-to-date copies of things that are important to me (namely my anime collection and /home) on an external 1TB drive that I always have on my body. My thought process here is if both the drive I carry and my computer are destroyed at the same time, I'd probably be dead too.
I also keep a similarly semi up-to-date backup of my server on the same drive. This backup is never as up-to-date as I'd like.
I use cronjobs and bash scripts to perform daily backups of my personal computer and server. These are stored on a drive dedicated to backups always mounted on my computer, in the case of my server - a mere directory. Every now and then I copy these backups to the drive I carry everywhere. These are single tar files gzip compressed. I completely understand having the backups mounted and accessible is not the right way to do things.
I keep these backups for a short period after which they are deleted and replaced with newer ones.
Local personal computer backup cronjob and script:
# cronjob # runs everyday at 1pm 0 13 * * * /home/daniel_j/programming/bash/backup/backup.sh # delete backups older than 5 days # runs every day at 3pm 0 15 * * * find /mnt/backups/tar_backups/old_backups/ -type f -mtime +5 -delete # backup script #!/bin/bash # move the last backup performed into the old backups directory mv /mnt/backups/tar_backups/*.tar.gz /mnt/backups/tar_backups/old_backups/ #backups tar -cvpzf /mnt/backups/tar_backups/home-backup-$( date '+%Y-%m-%d_%H-%M-%S' ).tar.gz /home > /dev/null echo "buzz=500" >/dev/tcp/localhost/3001(As a side note, the "echo "buzz" > /dev/tcp/localhost/3001" sends a command to an arduino that sounds a buzzer. I use it as an alert. I'll write more about this in another post.)
Server:
# cronjob # backup @daily /home/username/scripts/backup.sh # delete backups older than 2 days @daily find /home/username/backups/old_backups/ -type f -mtime +2 -delete # backup script #!/bin/bash # move the last backups performed into the old backups directory # (I backup both directories and an sql dump) mv /home/username/backups/*.tar.gz /home/username/backups/old_backups/ mv /home/username/backups/*.sql /home/username/backups/old_backups/ # backups # dump sql databases /usr/bin/mysqldump --all-databases > /home/username/backups/dump-$( date '+%Y-%m-%d_%H-%M-%S' ).sql -u root -pr00tpassw0rd # I backup everything valuable on / tar -cvpzf /home/username/backups/backup-$( date '+%Y-%m-%d_%H-%M-%S' ).tar.gz --exclude=/home/username/backups --exclude=/proc --exclude=sys --exclude=/mnt --exclude=/media --exclude=/run --exclude=/dev --exclude=/var/www/desu/f --exclude=/home/username/old_server --one-file-system / > /dev/nullAs for my anime collection, that is simply an rsync command.


Anime tracker
8/6/2018
MAL (MyAnimeList) recently forced every user with an account to reset their password, they say this is out of caution regarding an exploit they found within their API. A few days later the entire website disappears for days, completely inaccessible. They gave no explanation for this and weeks later many of their services are still unavailable.
Clearly, this is beyond acceptable. Through this disaster however came a new project idea.
I've began work on creating my own anime static anime tracker. You can find the goals of the project here.
There is a live version of the project here.
The source code can be found here, licensed under GPL2.


Miscellaneous RGB controller additions
13/4/2018
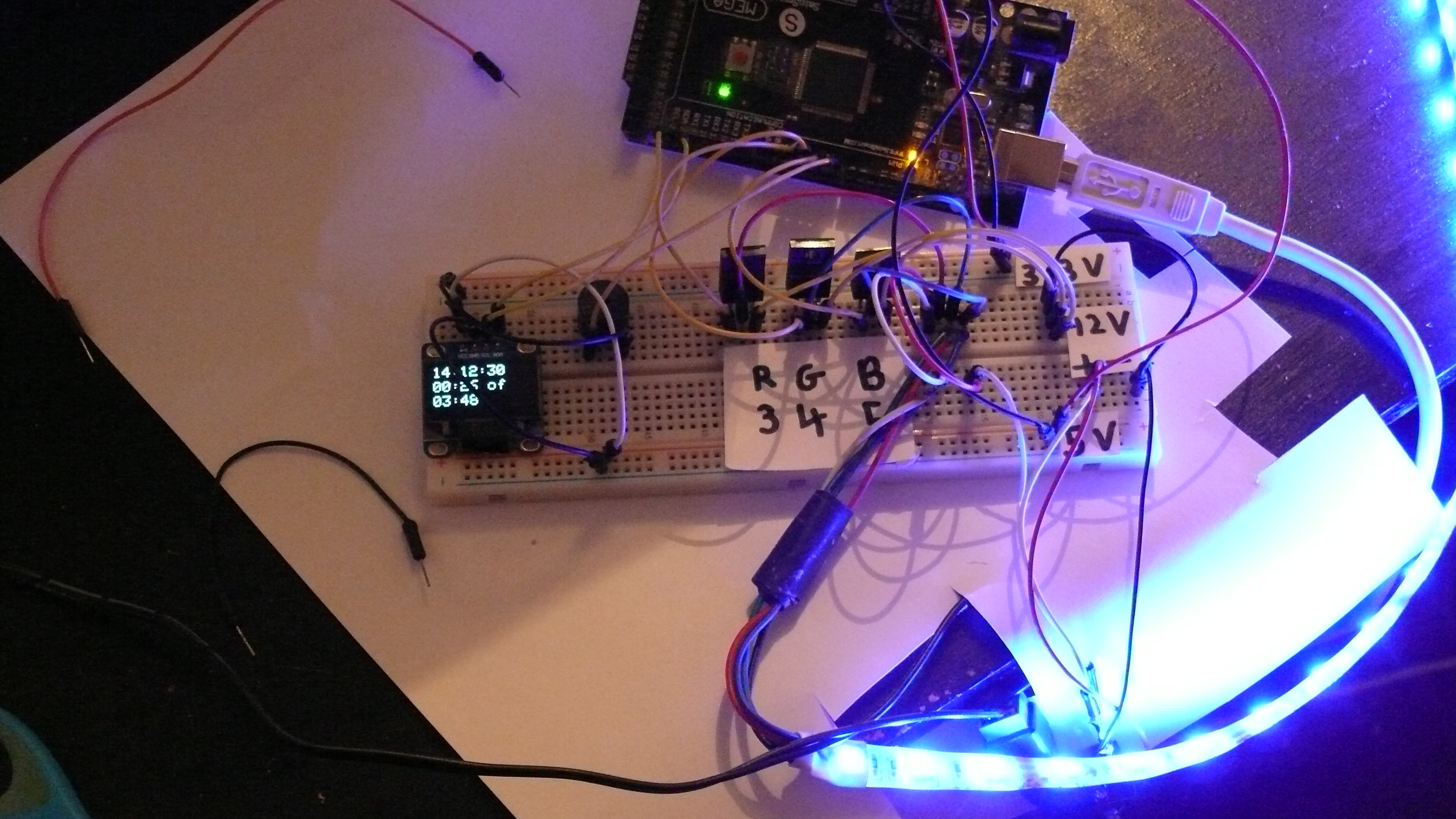
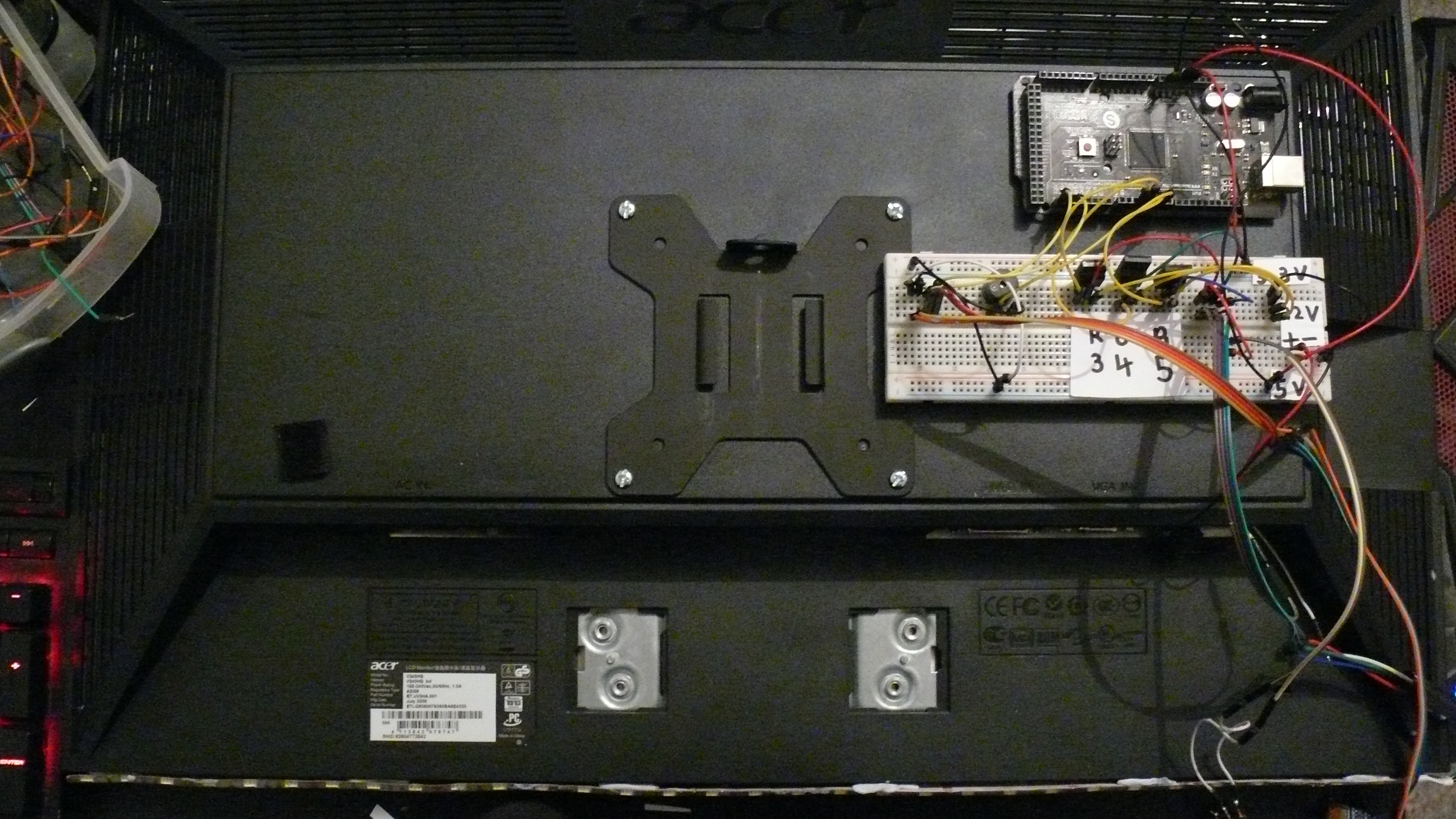
A month or two back I obtained a monitor arm in order to further reduce the clutter on my desk. Once setup I decided to get my RGB controller project back in a working order.
I ended up putting the strip to the underside of my monitor as well as mounting the arduino and accompanying breadboards on the back.
I added an oled display on the bottom of my monitor which currently displays the time and current song time/duration. This is achieved with a simple bash script. The arduino was programmed accordingly to receive and display the data. I also added a switch that controls the power going to the LED's. There is a slight leak of power when the RGB channels are set to 0 (meaning off), this switch allows me to kill the power supply entirely. Finally, I added a female power jack to make supplying the required 12v easier.
The code as always is available on git, now licensed under GPL 3.
The wiring is an absolute hackjob. I don't particularly enjoy wiring or working with components, let alone a soldering iron.


More things to mention
9/4/2018
New domain
Recently I acquired the domain 'gnupluslinux.com'. On a whim I had checked if such a domain was registered, .org was, however .com was available. I really had to have it.Currently I have https://i.use.gnupluslinux.com point to a listing of the software I use and the root domain https://gnupluslinux.com presents an explanation of what GNU plus Linux is. I also host my screenshots on the img subdomain currently.
The source of the website and its subdomains is appropriately available under the GNU GPL version 2 on git. If you're interested in hosting something on the domain (or optional subdomain), feel free to send a PR on GitHub or via email.
snake in c
I've been wanting some terminal games recently, instead of obtaining some from online it's much more entertaining to make my own. The first was snake.You can see an example of the game here and obtain the source code on git.


General things to mention
19/3/2018
No mouse
It has been well over a month now since I packed my mouse away and relied entirely on my keyboard for everything. After a week or so my teething problems were mostly sorted out, however to this day I still find myself using my tablet for screenshots and Reddit ModMail. However I rarely perform these two tasks and they are really non-issues.I have bound mod(+shift)+volume up/down (my keyboard has a volume wheel) to control the cursor for the other rare times in which I need to click on something (button on a website that can't be hinted for example) and so far that has worked well. I'm really quite happy with my progress with learning and relying on new keyboard oriented tools and shortcuts for doing everyday tasks. I have no desire or intention to go back to using a mouse.
Operating system
Two or so weeks ago I migrated my Arch Linux system to Parabola Linux-Libre. Parabola Linux-Libre is based on Arch Linux and is on the Free Software Foundations list of approved GNU/Linux distributions. The main modification is the use of the Linux-Libre kernel. The stock Arch kernel has proprietary blobs shipped with it, the Libre kernel strips those out. Parabola also comes with a package named your-freedom. your-freedom conflicts with every package available in the Arch repository that isn't free software, meaning you cannot install non-free software without removing your-freedom. This name is absolute genius. The switch was mostly painless - the hardest part was going through everything in the AUR I have installed and removing things that aren't free. However, now I am running (as far as I can tell) completely free software! Of course, apart from my bios... and I still have Intel ME... I'll get a t60 or x200 and libreboot it one day.School network
Similar to the exploit in TAFE's Force system I recently found, my school had a directory of private and confidential files free for anyone with an unprivileged network account to access. The network share held each staff members personal storage directory. These directories contained countless pieces of private and confidential documents on both students and the staff members themselves. This has been an existing issue since at least 2016. I reported the issue and it was fixed the next time I was in school.Directory permissions. They aren't rocket science. I fear what else lurks open for others to view on the network.
It's nice to get things off my chest.


High-level overview of binary
27/2/2018
For an upcoming school project I am producing multiple small pdfs explaining (in extremely high-level) binary, hexadecimal, ASCII and possibly some on general assembler languages. I don't have the best grasp on these subjects, so producing them on their own is good practice for me. The first one is on binary.
These documents are produced using pandoc+beamer.
The first pdf can be found here.